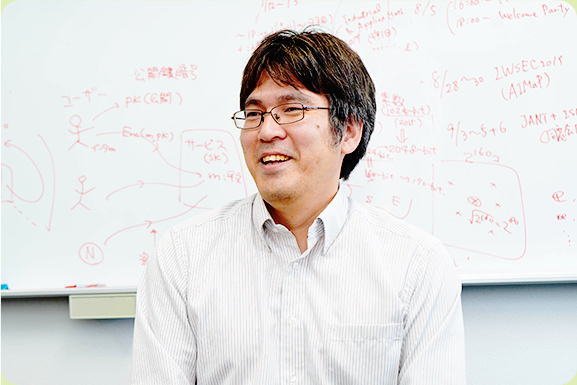
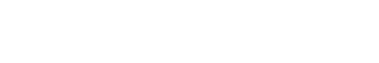Professor Yasuda thoughtfully explains that in mathematics, there are many ways to arrive at an answer. "What ultimately makes it so fascinating is the ability to find a straightforward solution."
Professor Yasuda thoughtfully explains that in mathematics, there are many ways to arrive at an answer. "What ultimately makes it so fascinating is the ability to find a straightforward solution."
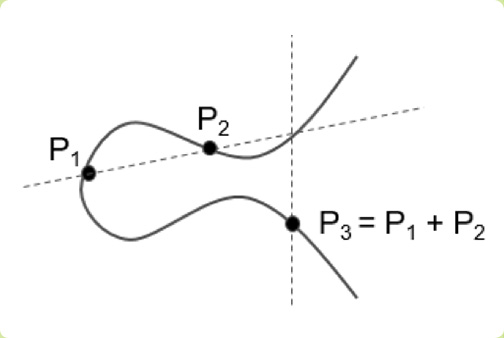 An elliptical curve is defined by the equation y2 = x3 + ax + b, which is used in public-key cryptography. This simple yet effective equation is an example of strength in numbers, with values that can stretch into the hundreds or thousands of digits.
An elliptical curve is defined by the equation y2 = x3 + ax + b, which is used in public-key cryptography. This simple yet effective equation is an example of strength in numbers, with values that can stretch into the hundreds or thousands of digits.
 Research materials on one of Professor Yasuda's computers. When teaching, Professor Yasuda always includes images to make difficult concepts easier to understand. These images and illustrations come in handy during his high school visits, he explains: "I'm not teaching if students aren't learning."
Research materials on one of Professor Yasuda's computers. When teaching, Professor Yasuda always includes images to make difficult concepts easier to understand. These images and illustrations come in handy during his high school visits, he explains: "I'm not teaching if students aren't learning."
 Professor Yasuda thoughtfully explains that in mathematics, there are many ways to arrive at an answer. "What ultimately makes it so fascinating is the ability to find a straightforward solution."
Professor Yasuda thoughtfully explains that in mathematics, there are many ways to arrive at an answer. "What ultimately makes it so fascinating is the ability to find a straightforward solution."
How do you use the internet? While we all enjoy the daily conveniences of online shopping and so many other online services, they come with the risk that our personal and confidential data could be leaked. As such, information security is one of the most important issues that we face in our modern internet society. For example, suppose you are booking a flight online. Your data is encrypted and sent to the service provider—in this case, the airline—where it is decrypted and used to process your request. Online encryption is what ensures that no one is eavesdropping on your data, often using one of two methods: RSA cryptography or elliptic-curve cryptography (ECC). Both are public-key cryptography systems that use two separate keys: one for encryption, which is made public, and one for decryption, which is kept secret.
 An elliptical curve is defined by the equation y2 = x3 + ax + b, which is used in public-key cryptography. This simple yet effective equation is an example of strength in numbers, with values that can stretch into the hundreds or thousands of digits.
An elliptical curve is defined by the equation y2 = x3 + ax + b, which is used in public-key cryptography. This simple yet effective equation is an example of strength in numbers, with values that can stretch into the hundreds or thousands of digits.
Different situations call for different encryptions. RSA cryptography is a secure form of encryption because of its long key size (or key length), but this uses a large amount of data, which slows down processing speeds. Credit card and online transactions are a familiar example of RSA encryption. Elliptic-curve cryptography, on the other hand, is lighter and faster than RSA cryptography. While RSA encryption is currently more widely used and can handle larger volumes of data, like the example of airline reservations, its key sizes are large at 2,048 bits, especially when compared to ECC keys, which require just 160 bits. My research focuses on ECC, which is commonly used for data protection in IC cards and student IDs, for copyright protection from piracy in Blu-Ray media, and to improve energy efficiency in electronic devices. ECC is also currently used in digital signatures of the cryptocurrency Bitcoin.
 Research materials on one of Professor Yasuda's computers. When teaching, Professor Yasuda always includes images to make difficult concepts easier to understand. These images and illustrations come in handy during his high school visits, he explains: "I'm not teaching if students aren't learning."
Research materials on one of Professor Yasuda's computers. When teaching, Professor Yasuda always includes images to make difficult concepts easier to understand. These images and illustrations come in handy during his high school visits, he explains: "I'm not teaching if students aren't learning."
Encryption technologies are derived from algorithms, which means that, in theory, they can be broken. Longer key lengths (larger amounts of data) require more time to crack, so theoretically the longer the key, the safer it is. But even the security of 1024-bit encryption, formerly a mainstream standard, was considered insufficient as of 2015. It is already estimated that 2048-bit encryption, the current recommended standard, will no longer be secure by 2030. While security has long been proportional to cost, with the advent of more advanced supercomputers, conventional encryption technologies may be cracked even earlier than expected. Competition is heating up around the globe as researchers race to develop next-generation encryption technologies like lattice-based cryptography.
With more and more research being published each day, cryptography has become one of the world's hottest industries. A recent conference in Japan drew close to 800 researchers. In 2010, a German university created a website where researchers from around the globe have continued to flock to compete in solving higher-order problems for next-generation encryption. For nearly ten years, everyone—my students and I included—has been trying to solve them. One of my students was even ranked 14th in the world at one point. As encryption continues to evolve, cryptography research, too, must try to keep up. And the more convenient the world becomes, the more secure data protection must be. So the question is, how can a mathematics-based approach to cryptography research help to integrate encryption into widely used services? Finding the answer to that question is my lifelong mission.


I love that I get to use mathematics for useful, real-world applications like encryption technology. My job is to make keys that are impossible to crack, which means that as I make them, I also have to learn how to break them. The field of cryptography is constantly flooded with dubious papers claiming to have developed some unbreakable cipher. There was once a paper that detailed a new and supposedly unbreakable type of encryption, to which I wrote an essay that refuted the claim and proved that this new encryption could, and would, be broken. [laughs] While there's always a definite answer to be found in mathematics, the subject itself is infinite. I'm always testing my decryption algorithms to find a key. It's a lot like my obsession with finding answers to math problems when I was a kid, which I think is why it's so interesting to me.
At the Institute of Mathematics for Industry, we link pure and applied mathematics with industry and science to help solve real-world mathematical challenges and develop much-needed technologies. Industry will often have a clear-cut problem that requires a technology for which the mathematical models don't exist yet. This means that the potential for research is infinite, and that's what makes this work so exciting—being able to create more opportunities for application.
![]()